Workforce Access
-
 15:59Watch Video
15:59Watch VideoDigital Ghosts: How to Find and Fix Orphaned Accounts Before Attackers Do
Orphaned accounts (inactive or unowned user identities that retain access to critical systems) represent one of the most overlooked security risks in modern enterprises.
-
 Read More
Read MoreWorkforce Identity Security Insurance Solution Brief
Secure access across brokers, claims, and underwriting with seamless identity protection built for modern insurance operations.
-
 Read More
Read MoreWorkforce Identity Security Retail Solution Brief
Deliver fast, secure access across POS, e-commerce, and vendor systems with identity protection designed for modern retail operations.
-
 Read More
Read MoreWorkforce Identity Security Built for Manufacturing
Protect manufacturing IP and operations with least privilege access, adaptive MFA, and session control for engineers, contractors, and OT systems.
-
 47:52Watch Video
47:52Watch VideoClosing SaaS Security Gaps: Protect Sessions Beginning to End
Learn to secure SaaS sessions with real-time monitoring and protection that won't disrupt your users.
-
 26:16Watch Video
26:16Watch VideoStrengthen Workforce Password Security with Platform-Powered Integrations
Learn how CyberArk Workforce Password Management integrates across the Identity Security Platform—and with third-party IdPs, PAM, Secure Web Sessions, and Enterprise Browser.
-
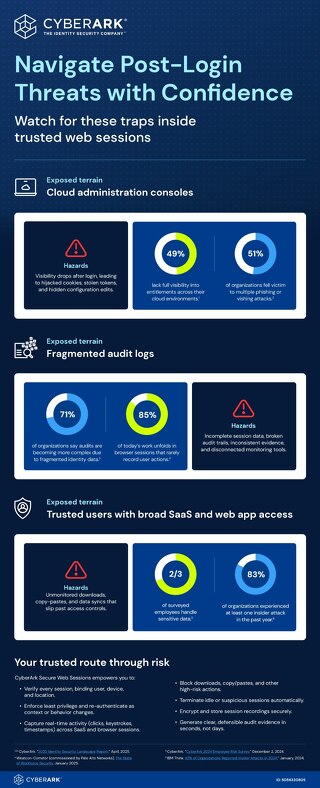 Read More
Read MoreNavigate Post-Login Threats with Confidence
This infographic highlights the hidden risks inside trusted web sessions and shows how CyberArk Secure Web Sessions delivers real-time visibility, control, and auditability to help organizations
-
 Read More
Read MoreMeet New NY Regulations with the CyberArk Identity Security Platform
Meet New York’s evolving 23 NYCRR 500 regulations with the CyberArk Identity Security Platform unified identity security for compliance, Zero Trust, & protection across financial services environment.
-
 23:45Watch Video
23:45Watch VideoFrom Login to Logout: Making Web Access Audit-Ready
In this session, CyberArk demonstrates how Secure Web Sessions (SWS) provides complete, audit-ready visibility and control over workforce web activity, helping organizations close compliance gaps,
-
 Read More
Read MoreCyberArk Workforce Password Management: Enabling CMMC Compliance and Stronger Identity Security
CyberArk WPM helps defense contractors meet CMMC compliance. It secures credentials with enterprise-grade password management, enforces strong policies, and provides detailed audit trails
-
 Read More
Read More3 Post-Login Threats That Keep CISOs Up at Night
Credentials are secure. Sessions are not. Learn how to detect and block post-login misuse before it becomes a breach.
-
 Read More
Read MoreStop Post-Login Threats with Secure Web Sessions
See and control what happens after login with PAM-grade oversight in every web session
-
 Read Blog
Read BlogThink IGA is challenging? You’re not alone
If getting visibility into and governance over your identity estate feels like a headache that—despite attempts at treatment—won’t go away, you’re not alone. You may have processes or tools, but...
-
 Read Blog
Read BlogSecrets, out: Why workload identity is essential for AI agent security
AI agents aren’t waiting in the wings anymore. They’re approving payments, spinning up cloud resources, and pulling sensitive data at machine speed. Blink, and a swarm of them has already acted a...
-
 Read More
Read MoreIdentity Security at a Crossroads: Balancing Stability, Agility, and Security
The latest ESG report explores how enterprises are navigating growing identity volumes, tool sprawl, and emerging risks like non-human identities and agentic AI.
-
 43:29Watch Video
43:29Watch VideoBeyond Passwords: How to Put Passkeys Into Practice
Join CyberArk and FIDO Alliance to explore how passkeys are redefining enterprise authentication.
-
 6:49Watch Video
6:49Watch VideoReimagining Access Management The Threat Landscape
Lavi Lazarovitz reveals how attackers target identity systems—and why it’s time to rethink access management in today’s evolving threat landscape.
-
 13:09Watch Video
13:09Watch VideoRe-Imagining Identity and Access Management for 2025
CyberArk’s Clarence Hinton explores key forces reshaping IAM and how organizations can rethink access management to meet today’s challenges.
-
 Read More
Read MoreCyberArk Secures Australia’s Critical Infrastructure
CyberArk completed an IRAP assessment at the Protected level, validating its Workforce Identity Security platform against Australia’s ISM and giving agencies the confidence to move sensitive workloads
-
 Read Blog
Read BlogCyberArk empowers Australia’s cyber resilience with IRAP assessment completion at the protected level
As ransomware strains hospital operations and supply‑chain attacks target energy grids, Australia’s public and regulated sectors need proven cyber resilience. At the heart of most breaches lie...
-
Loading More...


